Physical Address
304 North Cardinal St.
Dorchester Center, MA 02124
Physical Address
304 North Cardinal St.
Dorchester Center, MA 02124

A protocol of humanity (H) is a decentralized network built on Arbitrator This uses the biometric palm to check the vibrancy and identity of the user. Founded a team Experts in cryptography, distributed systems and privacy technology, humanity deals with increasing challenges of fraud based on AI, Sybil attacksAnd growing demand for verifiable, confident credentials.
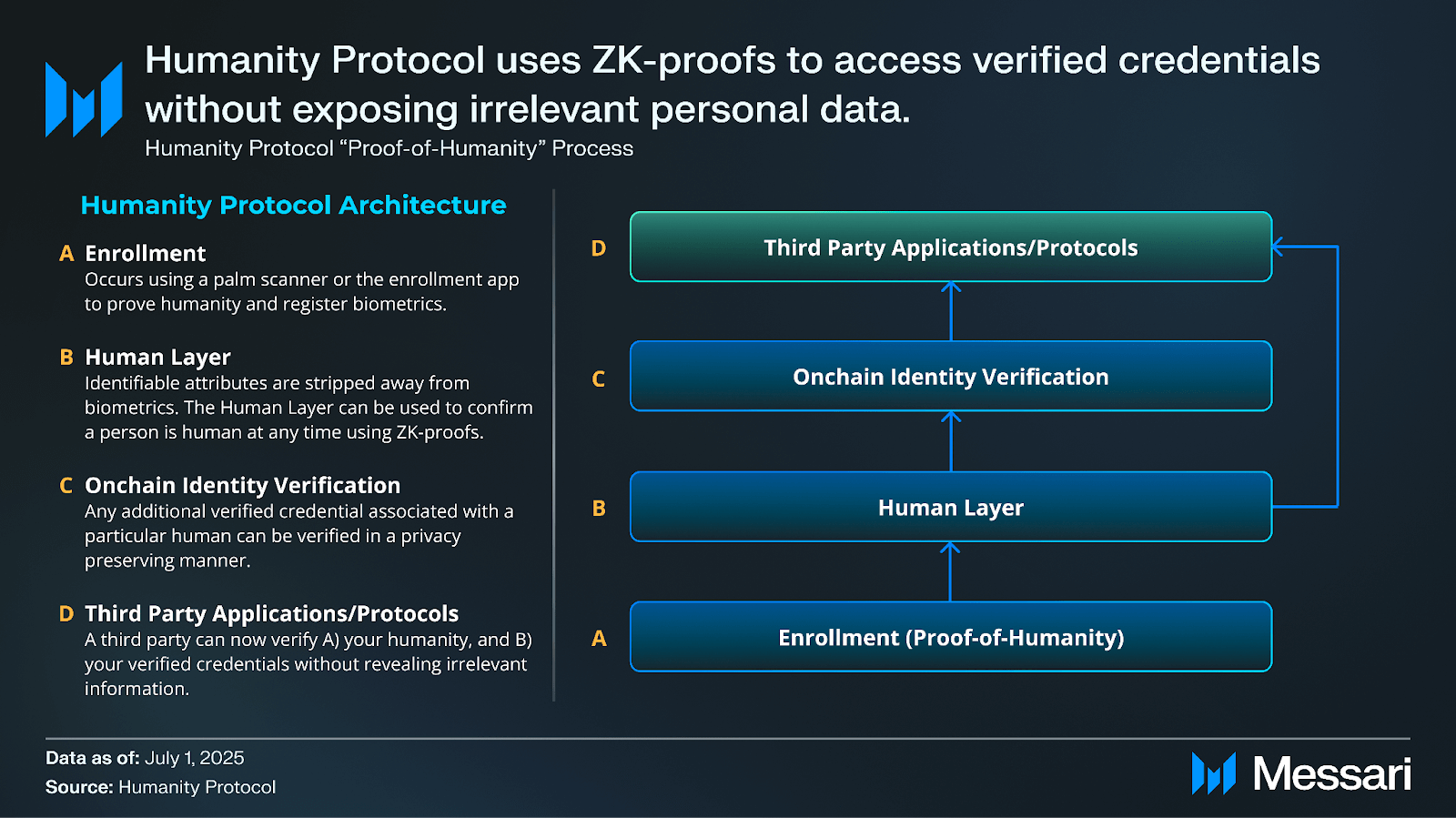
Humanity Proof of man Protocol uses palm scanners or a mobile app enroll and check people. Once the palm of the user is scanned, the protocol generates a cryptographic evidence that cannot be vice versa or associated with the original image, ensuring the storage of biometric data and the users retain control over their identity. Instead of storing biometric data, the system generates hash tied to a Human cardWhat can be checked by using Evidence of zero knowledge (ZK)a cryptographic method by which users can prove that they possess certain knowledge. This allows users to prove vibrancy or even individual traits such as age or residence, without detecting documents or biometric images. Users are respected by the surface prints of palm trees from the user’s mobile device or infrared vein scanners from PALM scanner to confirm the proven credentials.
AND H Token is the original property of the protocol of humanity and will be used for the incentives and management of validators. To ensure Sybil resistance from the beginning, the initial distribution of tokens was conducted through “Fair”, Approving h proven to human users, including early community associates, Kaito StavariMembers of disagreement and ecosystem builders.
Website / X / Disharmony / Telegram
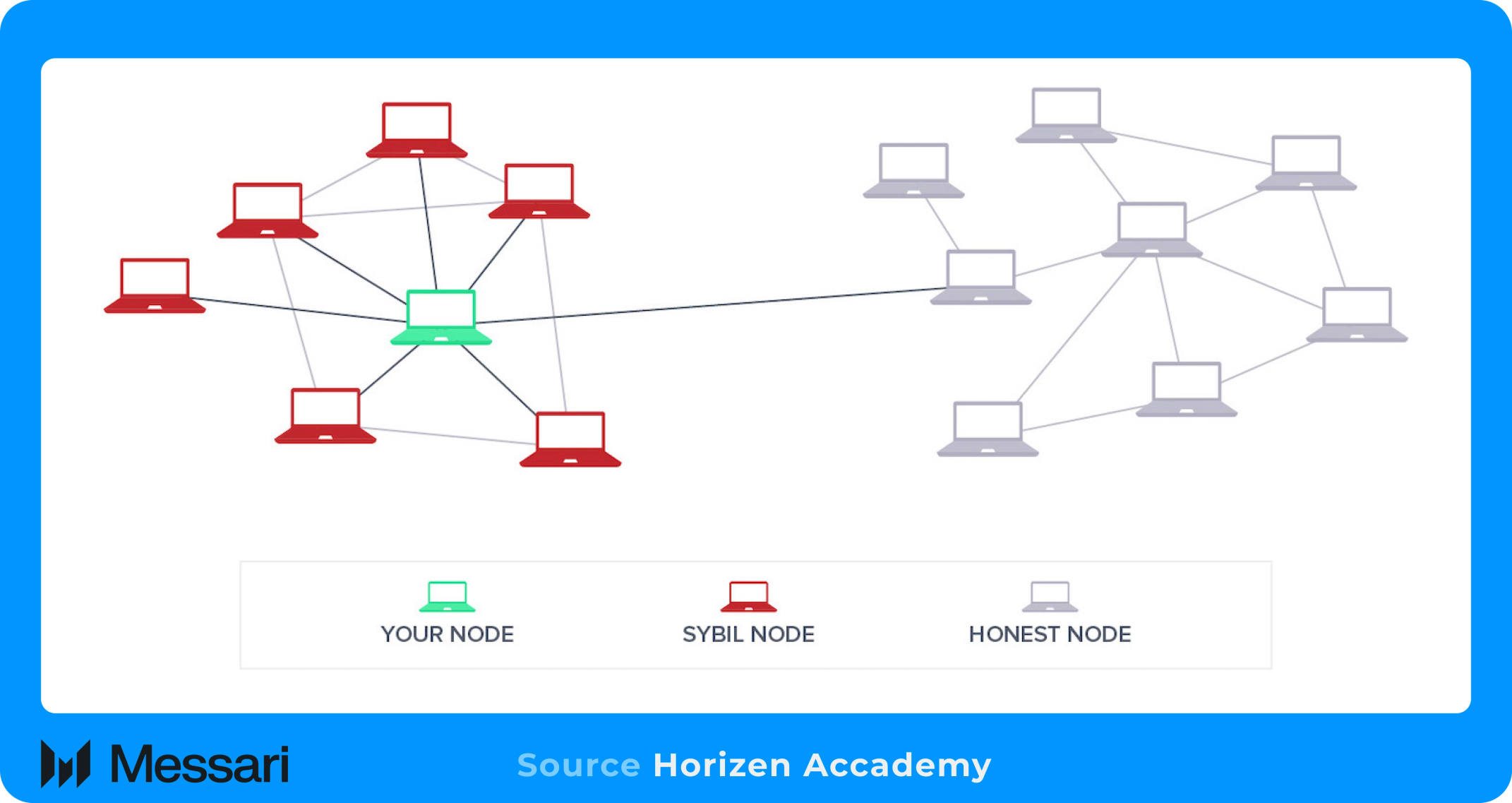
Sybil attacksIn which one entity creates and controls many false identities, he has long tormented digital ecosystems, undermining the righteousness of management and aircraft. If the network control is achieved, Sybil attacks can even result in a network censorship. The rise of Ai amplifies this problem, because bots can now imitate human behavior, generate convincing synthetic identities and bypassing traditional defense with increasing accuracy. As a result, the verification of humanity online has become a complex challenge with wide implications on trust, righteousness and security.
Conventional solutions are more and more inadequate. CaptainThe most disgusting line of the bott defense, now routinely bypasses AI. Stronger “Checking of Humanity”, including quizzes or behavioral analysis, often frustrate Real users until they manage to outsmart quickly develop bottles. In the meantime, the identity checks that they rely on the transfer of government id or personal data are not only intrusive and slow, but also expose sensitive data to the risks of abuse and breach.
Proof of man directly deals with these limitations. The protocol uses palm surface prints from a user’s mobile device or infrared vein scanner with palm scanners. The process involves scanning a user’s palm to create a cryptographic representation that cannot be revealed or connected to the original biometric image. This approach to protecting privacy ensures that raw biometric data or personal data are not stored on centralized servers, so that users retain complete control over their identity.
The humanity protocol extends the evidence of man Ondchain identity check system allowing proven users to generate and present Checked credentials (VC). Without exposure to fundamental data, these cryptographic certificates related to human ID confirm certain traits, such as age, stay or approach to events. This is achieved using a ZK-OTPORA. Users can show the possession of credentials, such as more than 18 years, without discovering their birth. The proof itself is sufficient to check and it is processed directly onchain. Credibility is not transformed and related to one human id, which prevents delegation or resale.
AND Total addressable market For the identity that keeps privacy, it includes web2 and web3, and are engaged in major companies such as Microsoft, Apple and Google. Cases of use of the market include voting,, air eyelidand applications limited in accordance with compliance such as Kyc (Know your customer) in Defining. In web2, Fintech,, educationand playing Sectors often require repeated KYC processes or validation of a third party credentials that could expose users unnecessary risk. The existing solutions are concentrated among centralized providers of services and intermediaries. A decentralized system that supports programming check in user -owned offers a structural alternative with a wide application.
Ai-ratio persons are getting harder to distinguish from actual users. Deepfakes I can now mimic voice, face patterns and high -loyalty typing behavior, eroding the trust on the network. Existing check tools, such as captains or behavioral filters, fail to detect synthetic actors on a scale and often degrade user experience.
The protocol of humanity is deals with the binding of a digital identity to a biometric check when enrolling. Each user is a cryptographic proven as a unique, living man. Unregistered people should present their palm (which deep rollers cannot achieve) and harmonize that palm in the future to greet their living.
Conventional KYC and identity identity check systems rely on the exchange of raw personal data, a privacy, compliance and security risk. In addition, companies must collect and store identity records for regulatory purposes, which increases operating directing costs and responsibility. The process is slow for users and exposes sensitive data with centralized systems with poor transparency. A more efficient approach to privacy conservation has become vital to increase regulatory pressure and users seek greater control over their data.
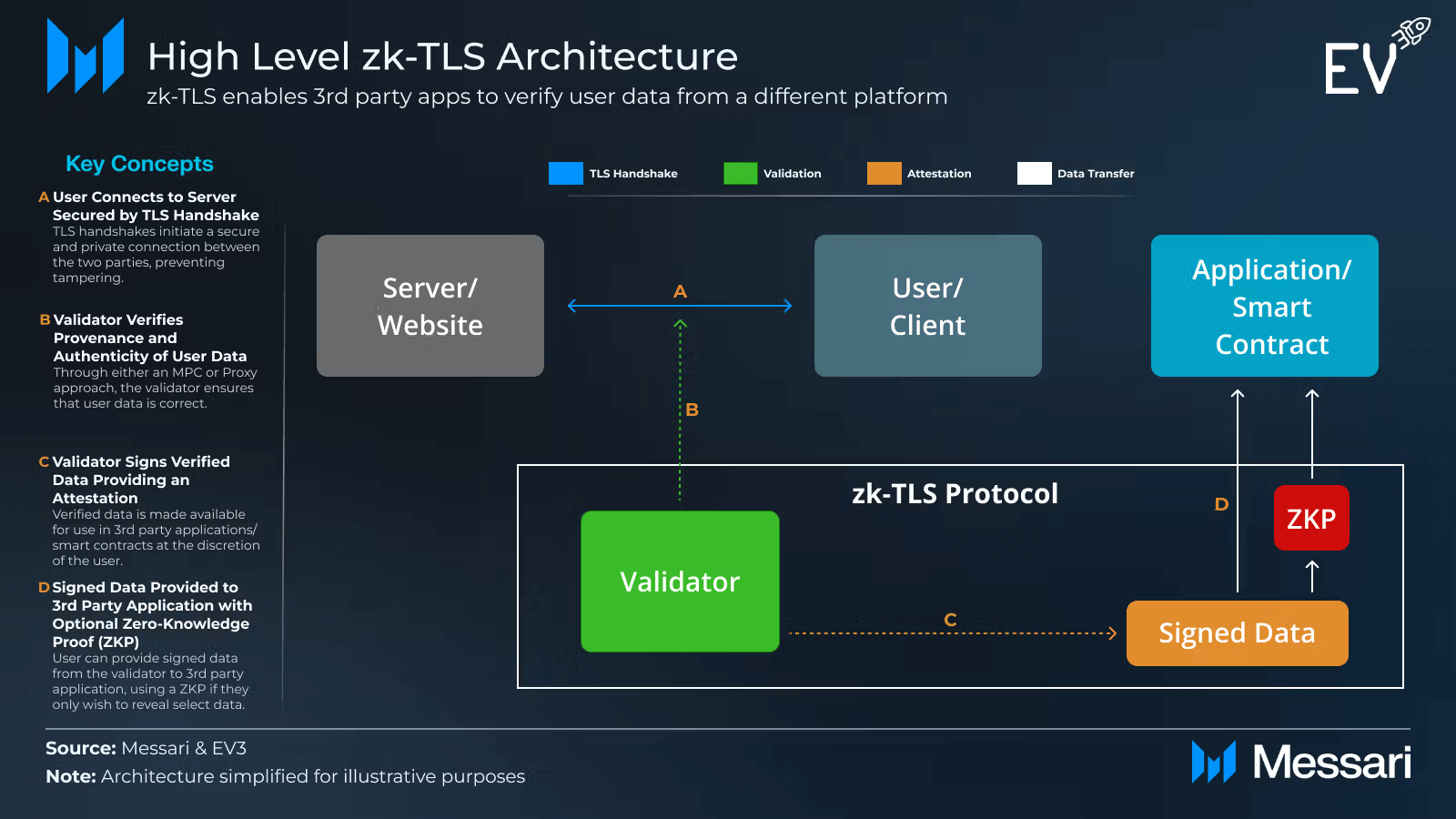
The framework of the ZK-TLS protocol of humanity replaces this model with cryptographic evidence. Instead of transferring documents, users can prove specific identity properties, such as human check or geographical eligibility, without detecting fundamental data. ZK-TLS notes a TLS hand grip (Allows two sides to authenticate through the Internet, establish a safe duct canal) between users and servers, allowing a validator to check attributes such as age or residence without exposing untreated data. The Validator signs the proven data that the user can turn into proof of zero knowledge and submit to the app. This allows third parties to confirm identity features without access to basic information.
ZK-TLS can be used in a series of identity settings, including:
Humanity’s network design preserves privacy, reduces the need to store data and support identity check in the web2 and web3 environments without addiction to central trust.
Ticket market faces Persistent problems with a bot scaling, forged sales and manipulation of resale. Existing systems often require identity detection to impose authenticity, but do not guarantee that tickets are issued or used by real people. As tickets move onchain, these problems reappear in new forms.
The protocol of humanity acquisition of Mongate brings a biometric identity to the ticket for sale of tickets. Tickets are issued directly to the human IDS cryptographicly related to a proven person using a hash. Because these IDs are not transferable and supported by evidence of zero knowledge, only real, unique users can request or use a map. Organizers may confirm the presence or approve of access after an event without a privacy. This design eliminates the need for documents based on documents, limits scaling at the protocol level and carries out ticket authenticity without the need for document transmission or the ID scan.
The protocol of humanity treats identity as a cryptographic primitive rooted in biological uniqueness. Replacing a system based on documents with a real -time -based check -based model is introduced by a model in which users can confirm who they are or what they qualify for without exposure to basic data. This reduces the risk of attack, limits exposure to data and creates a complex identity layer suitable for any application that requires confidence in human users.
The recent launch of H Token, distributed through the Sybil-proven human users’ fair fair, reflects the design of the protocol-the first design and commitment to decentralized participation from the very beginning. In addition to tools like ZK-TLS, the non-transferable human IDs and the acquisition of Moongate, the humanity protocol builds infrastructure for applications that require proven, private identity on web2 and web3. As identity becomes rooted in digital systems, the humanity protocol aims to get rid of the global market that extends in financing, management, AI and control of access in the real world.
Let us know what you loved in the report, which may be missing or sharing any other feedback Fulfilling this short form. All the answers are subject to our Privacy rules and Service conditions.
This report has ordered the protocol of humanity. All content was produced independently by the author (s) and does not necessarily reflect the opinions of Messari, Inc. or an organization who requested a report. The release organization may contribute to the content of the report, but Messari maintains editorial control over the final report to retain the accuracy and objectivity of the data. The author (s) can hold the crypto currency named in this report. This report is intended for information purposes only. Not intended to serve as an investment advice. Before making any investment decisions, you should implement your own research and consult with independent financial, tax or legal advisor. The effect of any property so far does not indicate future results. Please see ours Service conditions For more information.
No part of this report can be copied, photocopied, multiplied in any form in any way or (b) redistributed without prior written consent Messari®.